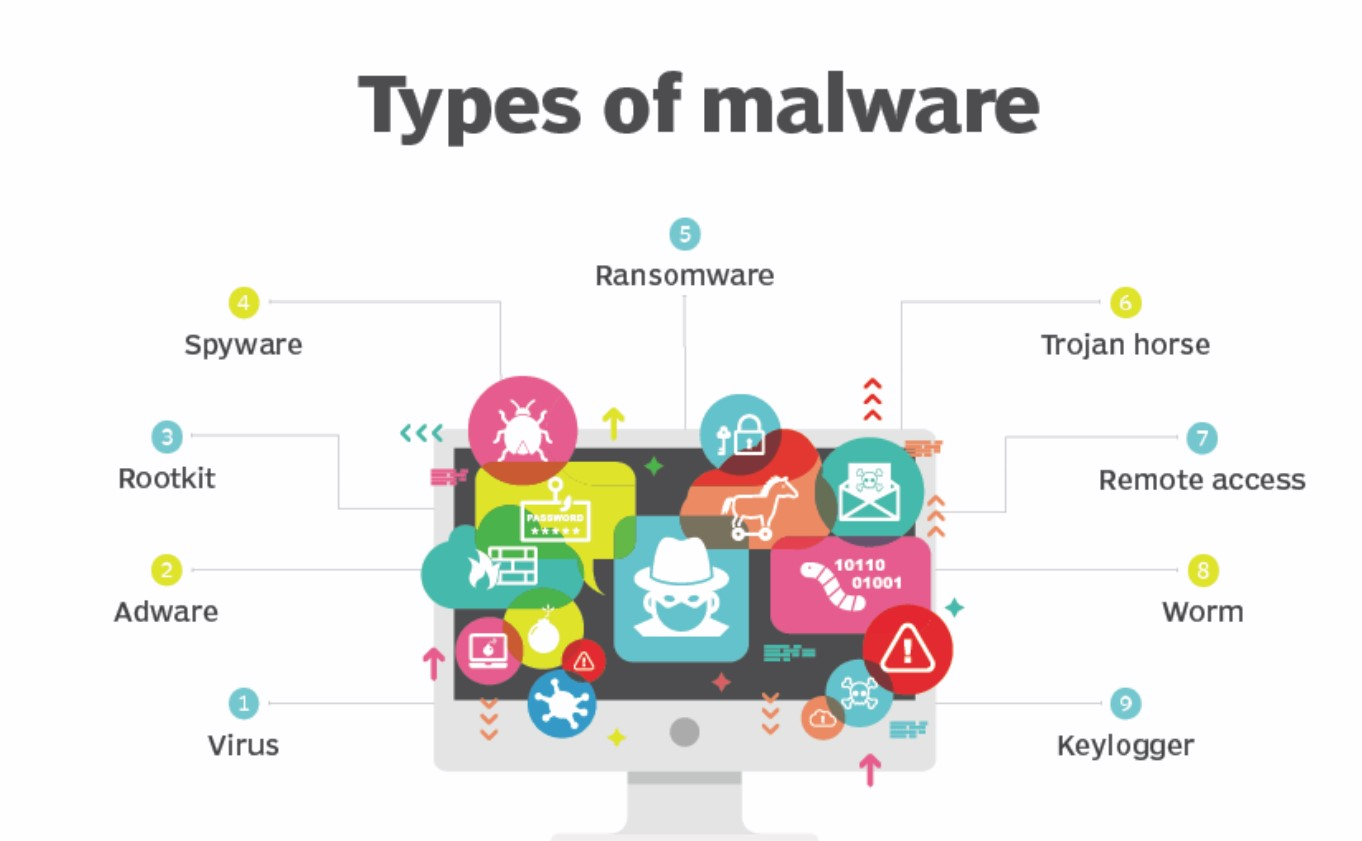
Ransomware poses a significant threat to individuals and organizations worldwide, encrypting valuable data and demanding payment for its release. In this guide, we’ll delve into the intricacies of detecting and removing ransomware from your system, providing detailed steps and insights to safeguard your data and restore system integrity.
Detecting Ransomware:
Antivirus Software Analysis:
- Utilize reputable antivirus software equipped with real-time scanning capabilities. These programs continuously monitor system activity, detecting and quarantining ransomware signatures and behaviors.
- Schedule regular full system scans to ensure comprehensive coverage against evolving ransomware threats.
File Extension Examination:
- Pay attention to files with unusual extensions such as .locky, .zepto, or .crypt. These are commonly associated with ransomware attacks.
- Employ file management tools or search functions to identify suspicious file extensions across your system.
Ransom Note Identification:
- Ransomware often leaves behind a ransom note, typically named “README.txt” or “DECRYPT_INSTRUCTIONS.txt.” Search your system for such files and take note of their locations.
- Analyze the content of these notes for instructions on ransom payment and decryption procedures.
Anomaly Monitoring:
- Monitor system behavior for anomalies such as sudden file encryption, unauthorized access attempts, or unusual network traffic patterns.
- Keep an eye on CPU and memory usage, as some ransomware strains exhibit increased resource consumption during encryption processes.
Removing Ransomware:
- Isolation and Containment:
- Immediately disconnect the infected system from the network to prevent further spread of the ransomware.
- Shut down any affected devices and refrain from accessing shared resources to contain the infection.
- Safe Mode Boot:
- Restart the infected system and boot into Safe Mode to minimize the ransomware’s ability to execute.
- Safe Mode limits the startup programs and services running on your system, facilitating the removal process.
- Antivirus Scan and Removal:
- Run a full system scan using your antivirus software, ensuring it is updated with the latest threat definitions.
- Follow the antivirus program’s instructions to quarantine or remove detected ransomware files and associated components.
- System Restore:
- If available, initiate a system restore to revert your system to a previous state before the ransomware infection occurred.
- Restore points created before the ransomware attack can help eliminate encrypted files and restore system functionality.
- Data Recovery from Backup:
- Restore your encrypted files from a clean backup source that predates the ransomware infection.
- Ensure the backup is free from ransomware contamination by scanning it with antivirus software before proceeding with data restoration.
- Specialized Ransomware Removal Tools:
- Explore the availability of specialized ransomware removal tools provided by reputable cybersecurity companies.
- These tools are designed to target specific ransomware strains, offering enhanced detection and removal capabilities.
- Professional Assistance:
- In cases of severe ransomware infections or uncertainty regarding the removal process, seek professional assistance from cybersecurity experts or IT professionals.
- Professional services can provide tailored solutions and guidance to address complex ransomware threats effectively.
Prevention Strategies:
- Regular Software Updates:
- Keep your operating system and software applications up to date with the latest security patches and updates.
- Patching known vulnerabilities helps mitigate the risk of ransomware exploitation.
- User Education and Awareness:
- Educate yourself and your organization’s members about common ransomware attack vectors, such as phishing emails and malicious attachments.
- Promote cybersecurity best practices, including skepticism towards unsolicited emails and caution when downloading files from unknown sources.
- Backup and Recovery Planning:
- Implement robust backup and recovery strategies to maintain copies of critical data in secure locations.
- Regularly backup your data to offline or cloud-based storage solutions, ensuring redundancy and resilience against ransomware attacks.
- Endpoint Security Solutions:
- Deploy endpoint security solutions equipped with ransomware protection features, including behavior-based detection and real-time threat prevention.
- Leverage advanced endpoint protection platforms to fortify your defense against evolving ransomware threats.
Detecting and removing ransomware from your system is crucial to safeguard your data and prevent further damage. Here’s a comprehensive guide on how to detect and remove ransomware effectively:
Detecting and Removing Ransomware: A Comprehensive Guide
Detection:
- Install Antivirus Software: Choose reputable antivirus software and keep it updated for real-time scanning.
- Update Operating System and Software: Regular updates patch security vulnerabilities exploited by ransomware.
- Education and Awareness: Train yourself and your team to recognize phishing attempts and suspicious links.
- Enable Firewall: Maintain an active firewall to block unauthorized access attempts.
- Behavior-Based Detection: Employ advanced antivirus programs that analyze behavior to detect ransomware.
Prevention:
- Regular Data Backup: Implement a consistent backup strategy to safeguard important files.
- Offline Backup Storage: Store backups offline or in secure, isolated environments to prevent compromise.
- System Monitoring: Regularly monitor system activity for unusual behavior or changes.
- Disconnect Infected Devices: Isolate infected devices from the network to prevent further spread.
- Identify Symptoms: Look for signs such as encrypted files, ransom notes, or system slowdowns.
Removal:
- Ransomware Removal Tools: Utilize antivirus software with specialized ransomware removal tools.
- Boot into Safe Mode: Limit malware’s ability to run by booting into safe mode.
- Full System Scan: Use antivirus software to perform thorough scans and remove ransomware.
- Restore from Backup: If available, restore files from a clean backup after removing the ransomware.
- Professional Assistance: Seek help from cybersecurity experts if unable to remove the ransomware or recover files.
- Update Security Practices: Review and enhance security measures to prevent future ransomware attacks.
By following these steps, you can effectively detect, remove, and prevent ransomware infections, safeguarding your data and minimizing the risk of financial loss. Stay vigilant and keep security practices up to date to counter evolving ransomware threats.