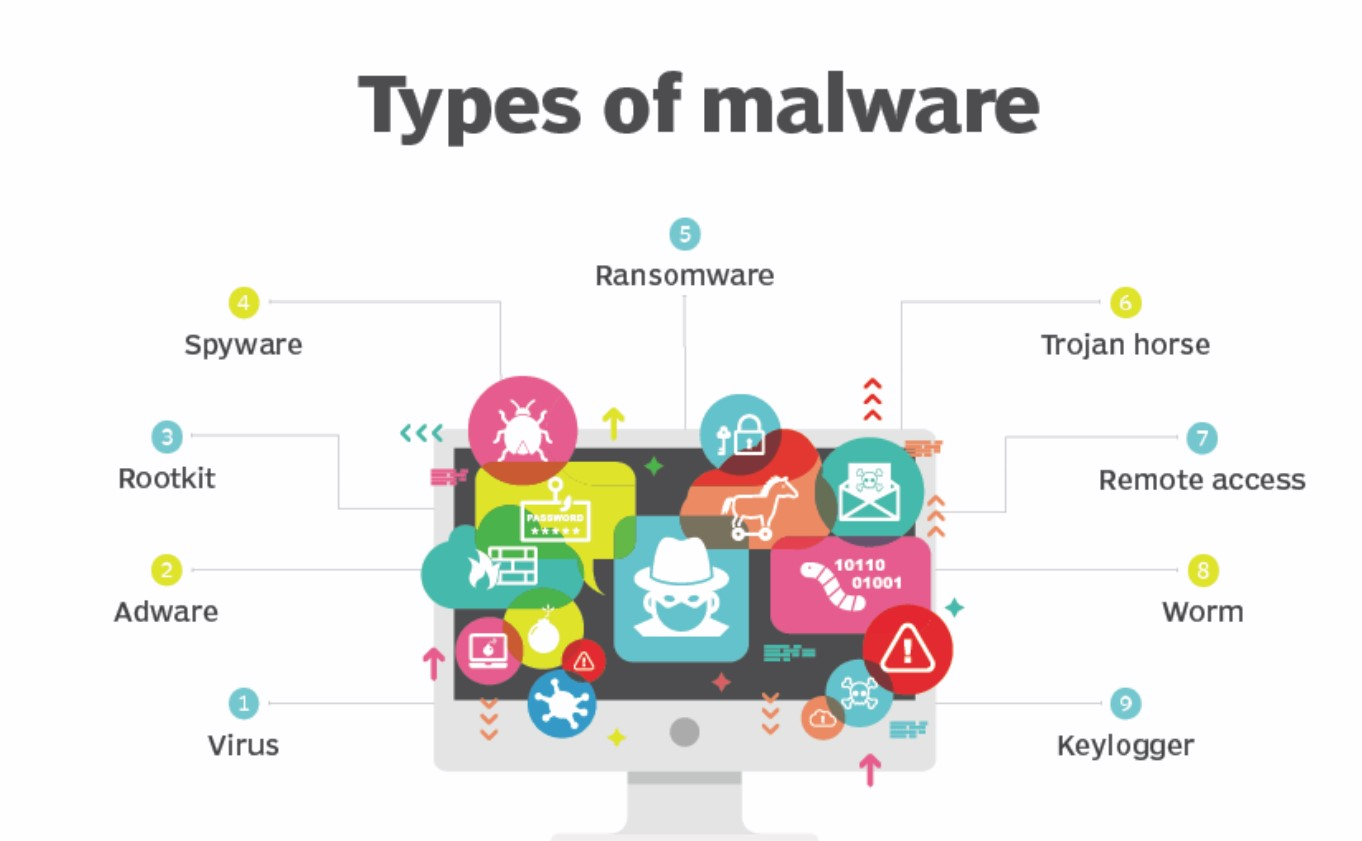
Malware in a website refers to malicious software that has been injected or implanted into the site’s files or code with the intent of causing harm, stealing data, or facilitating other malicious activities. This type of malware can compromise the security and functionality of the website, as well as pose risks to visitors. There are various types of malware that can affect websites, each with its own set of characteristics and potential impact.
Type of Malware:
There are various types of malware that can infect websites, each designed to achieve different objectives. Here are some common types of malware that can impact websites:
Viruses:
Web-based viruses infect website files and can spread to visitors’ computers when they download infected files. They may modify or delete files, disrupt website functionality, or facilitate other malicious activities.
Trojans:
Trojan malware disguises itself as legitimate software but carries malicious payloads. On websites, Trojans can be hidden in seemingly harmless files, exploiting vulnerabilities to gain unauthorized access or steal sensitive information.
Ransomware:
Ransomware on a website can encrypt files, rendering them inaccessible. Attackers then demand payment (often in cryptocurrency) for the decryption key, threatening to delete or permanently encrypt the data if the ransom is not paid.
Worms:
Web worms are self-replicating malware that can spread across networks and websites. They exploit vulnerabilities to automatically replicate and infect other web servers.
Spyware:
Spyware is designed to secretly collect information about users’ activities. On websites, spyware can track user behavior, log keystrokes, or capture sensitive information such as login credentials.
Adware:
Adware injects unwanted advertisements into websites, often disrupting the user experience and potentially leading to malicious websites or unwanted downloads.
Phishing Pages:
Malicious actors may compromise websites to host phishing pages. These pages mimic legitimate websites to trick users into entering sensitive information, such as login credentials or credit card details.
Drive-By Downloads:
Drive-by downloads occur when malware is automatically downloaded to a user’s device without their knowledge or consent when they visit a compromised website.
SQL Injection (SQLi):
SQL injection attacks exploit vulnerabilities in a website’s database by injecting malicious SQL code. This can lead to unauthorized access, data manipulation, or data theft.
Cross-Site Scripting (XSS):
XSS involves injecting malicious scripts into web pages that are then served to other users. This can be used to steal user data, session information, or spread malware to visitors.
Cross-Site Request Forgery (CSRF):
CSRF attacks trick users into performing actions on a website without their knowledge or consent. This can lead to unauthorized changes in user settings or data manipulation.
Backdoors:
Backdoors provide unauthorized access to a website, allowing attackers to control the site remotely. They can be used to upload additional malware, steal data, or perform other malicious activities.
SEO Spam:
Malicious actors may compromise websites to inject hidden links or content for the purpose of search engine optimization (SEO) spam. This can lead to the site being penalized by search engines.
Cryptojacking:
Cryptojacking involves using a website visitor’s device to mine cryptocurrency without their consent. This can slow down the user’s device and increase energy consumption.
File Inclusion Exploits:
File inclusion exploits involve manipulating a website’s code to include malicious files. This can lead to remote code execution and unauthorized access.
Preventing malware attacks:
Preventing malware attacks on a website involves implementing a combination of security measures and best practices. Here are several steps you can take to help protect your website from malware:
Keep Software and Plugins Updated:
Regularly update your website’s content management system (CMS), plugins, themes, and any other software. This helps patch vulnerabilities and reduces the risk of exploitation.
Use Strong Authentication:
Enforce strong passwords for all user accounts, and use multi-factor authentication (MFA) whenever possible to add an extra layer of security.
Regular Security Audits:
Conduct regular security audits of your website to identify and address vulnerabilities. This can include code reviews, penetration testing, and vulnerability scanning.
Implement HTTPS:
Use HTTPS to encrypt data transmitted between the user’s browser and your website. This not only enhances security but also boosts your website’s search engine ranking.
Backup Your Website:
Regularly backup your website’s data and files. In the event of a malware attack, you can restore your website to a clean state. Store backups in a secure location separate from your website server.
Secure File Uploads:
If your website allows file uploads, ensure that you implement proper security measures to prevent malicious uploads. Limit allowed file types, use file type verification, and scan uploads for malware.
Implement Web Application Firewalls (WAF):
WAFs can help filter and monitor HTTP traffic between a web application and the Internet, providing an additional layer of security against various types of attacks, including those from malware.
Monitor User Activity:
Regularly review and monitor user activity on your website. Look for unusual patterns, unexpected changes, or suspicious behavior that could indicate a security compromise.
Use Security Headers:
Implement security headers in your website’s HTTP responses to provide additional security layers. Examples include Content Security Policy (CSP), Strict Transport Security (HSTS), and X-Content-Type-Options.
Educate Users and Staff:
Train website administrators and users to recognize and avoid phishing attempts, suspicious emails, and social engineering tactics. Awareness is a critical component of overall security.
Limit User Permissions:
Grant the minimum necessary permissions to users and administrators. Avoid using administrator accounts for routine tasks to reduce the impact of a potential compromise.
Regularly Scan for Malware:
Use website security tools and scanners to regularly check for malware and vulnerabilities. Many security tools can provide real-time alerts and automated scans.
Implement Content Security Policies (CSP):
CSP helps prevent cross-site scripting (XSS) attacks by defining and controlling which resources can be loaded on your website. It limits the execution of scripts and mitigates the impact of XSS vulnerabilities.
Regularly Check for Blacklisting:
Monitor if your website is blacklisted by search engines or security organizations. Being blacklisted can impact your site’s reputation and visibility.
Monitor Third-Party Integrations:
If your website relies on third-party services or scripts, regularly monitor and update them to ensure they are secure. Remove any unnecessary integrations.
By adopting a proactive approach to website security and staying vigilant, you can significantly reduce the risk of malware attacks. Regularly updating, monitoring, and educating all stakeholders are key elements in maintaining a secure online presence.
To protect a website from malware, it’s crucial for website owners and administrators to follow security best practices, including regular updates, strong authentication, secure coding practices, and monitoring for suspicious activities. Implementing security measures and conducting regular security audits can help identify and address potential vulnerabilities before they are exploited by malicious actors.